Internet Basics Solved MCQs 1. The acronym w3c stands for _________ world web wide. wide world web world wide web world wide w...
Internet Basics Solved MCQs
1.The acronym w3c stands for _________
- world web wide.
- wide world web
- world wide web
- world wide web control
C. world wide web
2.HTML is a ______ language
- procedural
- markup
- object oriented
- object based
B. markup
3.HTML documents stored in the file in the form ______
- .hxm
- .html or .htm
- .hm
- .hml
B. .html or .htm
4.To change xxxx@yyyy.zzzz to an IP address, we should use the _______ protocol
- TELNET
- DNS
- NVT
- none of the above
B. DNS
5.Match the following terms: 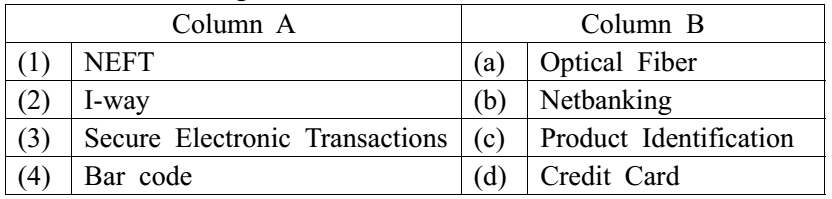

- 1-d, 2-b, 3-a, 4-c
- 1-d, 2-c, 3-b, 4-a
- 1-d, 2-a, 3-b, 4-c
- 1-b, 2-a, 3-d, 4-c
D. 1-b, 2-a, 3-d, 4-c
6.Which of the following is not a C2C business model?
- Manufacturer’s website for selling home appliances online
- Website for auctioning used goods
- Website for posting content related to selling and/or buying houses
- Website allowing anyone to publish advertisements related to selling and/or buying cars
A. Manufacturer’s website for selling home appliances online
7.Electronic wallets refer to
- Website selling electronic appliances online
- Mechanism for secure e-payments
- Wallets housing smart/credit/debit cards
- Wallets fitted with electronically operated locks
B. Mechanism for secure e-payments
8.Match the following terms: 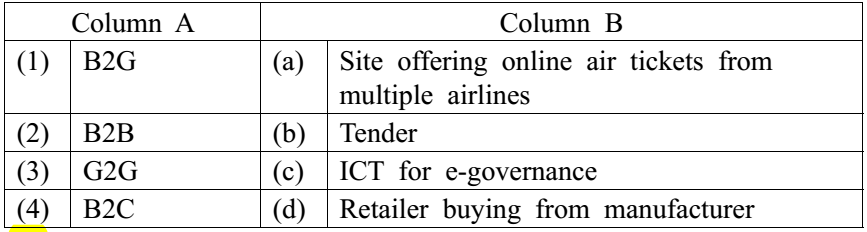

- 1-b, 2-d, 3-a, 4-c
- 1-d, 2-c, 3-b, 4-a
- 1-d, 2-a, 3-b, 4-c
- 1-b, 2-a, 3-d, 4-c
A. 1-b, 2-d, 3-a, 4-c
9.Digital Library of India is a library with
- printed books about e-Commerce, e-governance and ICT
- computerized issue/renewal/return of books
- library with collection of books in PDF format
- computers with Internet facility for catalogue and web browsing
C. library with collection of books in PDF format
10.COBIT was an acronym for
- Cost of Business in Information Technology
- Control Objectives for Information and Related Technology
- Computerization of Business Intelligence Techniques
- Computerization of Information Related Technology
B. Control Objectives for Information and Related Technology
Practice it now
1.Which of the Following is correct special charecter Code
- & code
- & amp
- & copy.
- # code
B. & amp
2.By default, ordered list use _____ sequence of numbers
- octal
- hexadecimal
- binary
- decimal
D. decimal
3.The _____ element is used to insert a horizontal rule.
- hr
- rule
- rh
- line
A. hr
4.In ERP, data migration refers to
- Upgrading ERP software
- Upgrading both hardware and ERP software
- backup of data on an ERP system
- moving, copying and restructuring data from an existing system to the ERP system
D. moving, copying and restructuring data from an existing system to the ERP system
5.Which of the following depicts correct chronological order for scope of COBIT framework
- Management, Audit, Control, IT Governance, Governance of Enterprise IT
- Control, Audit, Management, IT Governance, Governance of Enterprise IT
- Audit, Control, Management, IT Governance, Governance of Enterprise IT
- Governance of Enterprise IT, Audit, Control, Management, IT Governance
C. Audit, Control, Management, IT Governance, Governance of Enterprise IT
6.HTTP is
- Request-Response Protocol
- Stateful
- Secured
- All of above
A. Request-Response Protocol
7.The default size of block in Apache HDFS is
- 512 bytes
- 64 MB
- 1024 KB
- None of the above
B. 64 MB
8.Payment Gateway refers to
- a merchant service authorizing payments for e-businesses
- a merchant service to resolve financial disputes
- networking switch at a bank/financial institution
- none of the above
A. a merchant service authorizing payments for e-businesses
9.“Collaborative application development” means
- software development by a team of developers
- software targeting many applications
- opening the source code of application/components for other developers
- outsourcing application code development
C. opening the source code of application/components for other developers
10.Electronic data interchange means
- a software for copying data from one computer to another
- a software for synchronizing data across many devices
- import/export of electronic devices used for data storage
- sets of formats/standards used for electronic exchange of business information
D. sets of formats/standards used for electronic exchange of business information
Practice it now
1.Types of entities are called _______
- parameter entities.
- ignore entities.
- percent entities
- normal entities.
A. parameter entities.
2.Types of entities are called _______
- parameter entities.
- ignore entities.
- percent entities
- normal entities.
A. parameter entities.
3.XML documents are called ________ sections
- CDATA
- EDATA
- scripting code.
- parser
A. CDATA
4.The ____ and ______ attributes specify the layout of frames within the browser window.
- frames and frameset.
- font and style.
- cols and rows
- forms and fonts.
B. font and style.
5.The ________ attribute in an input element inserts a button that, when click will clear the contents of reset.
- type =”reset”
- ype = “input”.
- type = “thread”.
- type = ” “.
A. type =”reset”
6.CSS introduces the position property and a capability called ________.
- absolute
- position property.
- positioning
- positioned
A. absolute
7.Which of the following is not correct?
- 110101002 = 324 base 8
- 01 1011 0100 base 2 = 2B4 base 8
- 1 01 01 0 110 base 2 = 526 base 8 = 156 base 16
- 34 base 8 = 24 base 16
D. 34 base 8 = 24 base 16
8.Match the following terms: 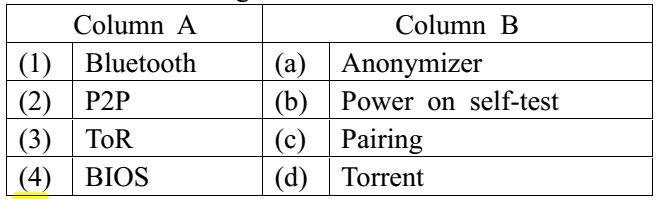

- 1-c, 2-d, 3-a, 4-b
- 1-d, 2-c, 3-b, 4-a
- 1-d, 2-a, 3-b, 4-c
- 1-b, 2-a, 3-c, 4-d
A. 1-c, 2-d, 3-a, 4-b
9.To represent one billion (1 billion = 1000 million), minimum number of bits needed are
- 12
- 30
- 15
- 20
B. 30
10.Match the following terms: 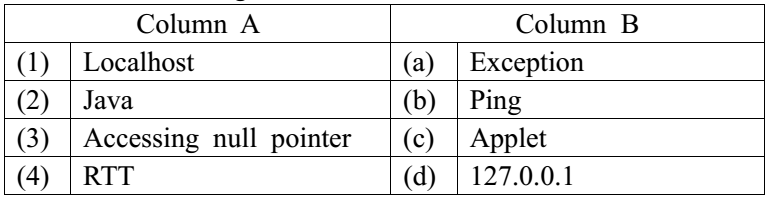

- 1-c, 2-d, 3-a, 4-b
- 1-b, 2-a, 3-c, 4-d
- 1-d, 2-c, 3-b, 4-a
- 1-d, 2-c, 3-a, 4-b
D. 1-d, 2-c, 3-a, 4-b
Practice it now
1. ________ element is a grouping element
- dw
- Span
- Span, dw.
- italic
B. Span
2.A language that is used for creating other languages is called __________
- markup language
- meta language
- schema language
- software language
B. meta language
3.All XML documents must contain exactly one _____
- root element.
- prolog
- child element.
- function
A. root element.
4.Lines preceding the root element are the ______ of the XML document
- child
- function
- prolog
- comments
C. prolog
5.a software program is called, ______ is required to process an XML document
- XML object model
- XML compiler.
- XML parser
- XML Interpreter.
C. XML parser
6.An XML document is considered to be syntactically incorrect if ___________
- contains a start tag & end tag.
- properly rested tags.
- attribute values in quotes
- contains two root elements
D. contains two root elements
7. _______ is an example for an application that has a built in XML parser
- Microsoft Internet Explorer (IE5).
- Google chrome
- Epic
- Mozilla Firefox
A. Microsoft Internet Explorer (IE5).
8.An element that contains a plus sign next to it, is called _________.
- pixel element.
- positive element.
- style sheet element
- container element
D. container element
9.________ enables computer to process the characters for most of the world’s major languages.
- Multicode
- ASCII code
- Unicode
- Text code
C. Unicode
10.________ is enclosed in angle brackets.
- Character data.
- Markup text.
- Container element.
- Procedure
B. Markup text.
Practice it now
1.________ is the text between a start and an end tag.
- Markup text
- Container element
- Procedure
- Character data
D. Character data Explanation :
2.Space, tabs, line fields and carriage returns are examples for ________
- special references
- special elements
- special text.
- White Space
D. White Space Explanation :
3.The process of converting insignificant whitespace characters into a single white space character or entirely removing it is called ___________
- interchanging
- preservation
- normalization
- comparison
C. normalization
4.________ begins with an ampersand and end with a semi colon.
- White spaces
- Character data
- Text elements
- Entity references
D. Entity references
5.The ______ file defines the structure of the XML document.
- DLL extension
- DTD extension
- XML extension
- DDT extension.
B. DTD extension Explanation :
6.“Hotspot” refers to
- most heated part of computer system
- region where there is no network
- region with internet access using wi-fi
- a heat sink
C. region with internet access using wi-fi
7.Which of the following is not a required component of Aadhaar card issued by UIDAI?
- Face image
- Fingerprint Image
- Iris image
- Voice recording
D. Voice recording
8.Which of the following techniques is employed for improving transmission efficiency of digital documents?
- Encryption
- USB
- Compression
- Steganography
C. Compression
9.Which of the following does not require OCR software component?
- Assistive technologies
- Extracting text from scanned documents
- Face recognition
- License number identification
C. Face recognition
10.A captcha is used for verifying if a web-user
- is a machine or a human being
- is frequent or infrequent visitor
- has logged out
- is a registered user or not
A. is a machine or a human being
Practice it now
1.Which of the following is true for HTML?
- Browser displays only body part
- Browser displays only header part
- Browser displays body and header both
- None of the above
A. Browser displays only body part
2.URL includes
- Protocol type
- Path of web resource
- Domain Name and Port Number
- All of above
D. All of above
3.Which of the following software is not a web server?
- Apache
- Internet Information Services (IIS)
- Mongoose
- Python
D. Python
4.In HTML, colour code #FF7F3F represents a color in which intensity levels of primary colors are
- Red = 255, Green = 127 and Blue = 63
- Blue = 255, Green = 127 and Red = 63
- Green = 255, Blue = 127 and Red = 63
- Invalid color code
A. Red = 255, Green = 127 and Blue = 63
5.In Internet communication, ‘‘cookie’’ is used for
- storing authentication information at server side for entire session
- storing authentication information at client side for entire session
- detecting intrusion at client side for entire session
- detecting intrusion at server side for entire session
A. storing authentication information at server side for entire session
6.Which of the following is not system software?
- WinZip
- Compiler
- Virtual Machine
- YACC
A. WinZip
7.Which of the following E-commerce model is also a part of E-governance?
- B2B
- G2C
- B2C
- C2C
B. G2C
8.Match the following terms: 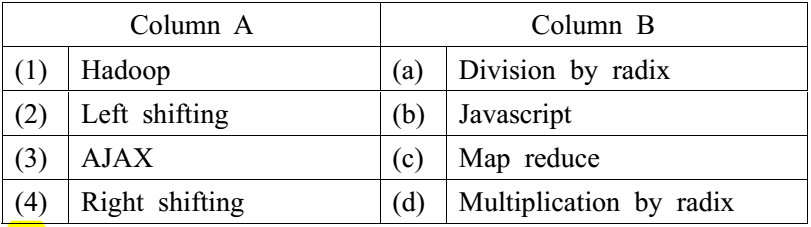

- 1-c, 2-d, 3-b, 4-a
- 1-c, 2-a, 3-b, 4-d
- 1-d, 2-c, 3-a, 4-b
- 1-d, 2-b, 3-a, 4-c
A. 1-c, 2-d, 3-b, 4-a
9.A cross-compiler is a
- compiler for object oriented languages
- compiler for JAVA written in C
- compiler that can generate machine codes for other platform
- compiler for non-procedural languages
D. compiler for non-procedural languages
10.Basic XML can be described as:
- A hierarchical structure of tagged elements, attributes and text.
- All the HTML tags plus a set of new XML only tags.
- Object-oriented structure of rows and columns.
- Processing instructions (PIs) for text data.
A. A hierarchical structure of tagged elements, attributes and text.
Practice it now
1.A client _______ a service.
- requests
- provides
- a or b
- a and b
A. requests
2.A server _______ a service
- requests
- provides
- a or b
- a and b
B. provides
3.WiFi is a short name for ___________
- Wired Fidelity
- Wireless Fidelity
- Wireless Frequency
- None of above
B. Wireless Fidelity
4.Responsibility of implementation of IT/ITeS Policy lies with
- State Technology park Unit
- Ministry of IT at State and Center
- Director (IT) in consultation with DST
- Industrial Commissioner
C. Director (IT) in consultation with DST
5.In India Subject to a ceiling of Rs. 25 crores, Capital Subsidy for Horizontal IT/ITeS Parks shall be
- 10% of fixed capital investment (excluding the cost of land)
- Rs. 200 per sq. ft. for built-up area
- 25% of fixed capital investment (excluding the cost of land)
- Rs. 300 per sq. ft. for built-up area
C. 25% of fixed capital investment (excluding the cost of land)
6.Match the following terms: 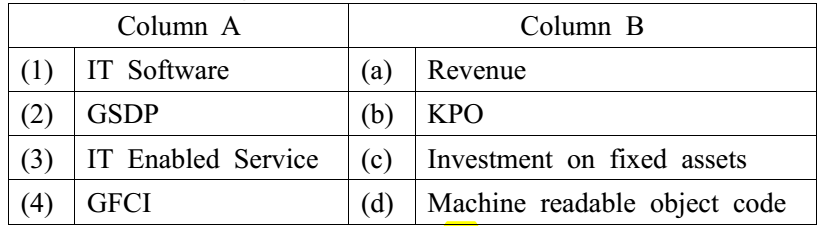

- 1-d, 2-b, 3-a, 4-c
- 1-d, 2-c, 3-b, 4-a
- 1-d, 2-a, 3-b, 4-c
- 1-b, 2-a, 3-d, 4-c
C. 1-d, 2-a, 3-b, 4-c
7.In As per IT/ITeS Policy (2016-21), term BPO refers to
- Business Process Outsourcing
- Business Process Outcomes
- Best Processing Outcomes
- Business Practices and Outcomes
A. Business Process Outsourcing
8.In india Which of the following is not CORRECT about “DigiLocker”?
- Signing for DigiLocker requires an individual’s mobile number
- DigiLocker is a platform for issuance and verification of documents & certificates in a digital way, thus eliminating the use of physical documents.
- Organizations registered with DigiLocker can store electronic copies of documents/certificates directly into citizens’s lockers.
- Citizens can download e-documents but can not upload any document in their accounts.
D. Citizens can download e-documents but can not upload any document in their accounts.
9.Match the following terms: Applicable to india 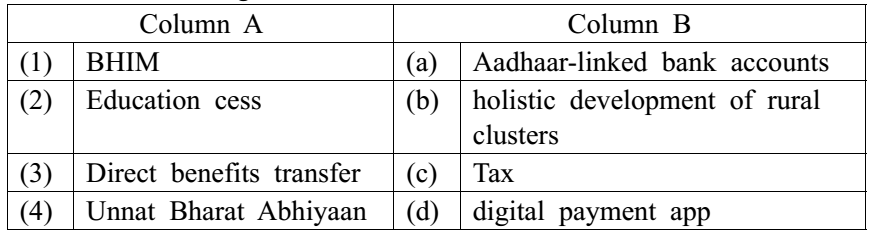

- 1-b, 2-d, 3-a, 4-c
- 1-b, 2-c, 3-d, 4-a
- 1-d, 2-a, 3-b, 4-c
- 1-d, 2-c, 3-a, 4-b
D. 1-d, 2-c, 3-a, 4-b
10.Match the following terms: 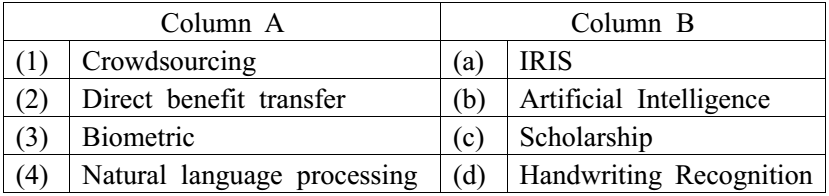

- 1-b, 2-d, 3-a, 4-c
- 1-d, 2-c, 3-a, 4-b
- 1-d, 2-a, 3-b, 4-c
- 1-d, 2-c, 3-b, 4-a
B. 1-d, 2-c, 3-a, 4-b
Practice it now
1.To change an IP address to xxxx@yyyy.zzzz, we should use the _______ protocol
- TELNET
- DNS
- NVT
- none of the above
B. DNS
2.Internet is
- a local computer network
- a world wide network of computers
- an interconnected network of computers
- a world wide interconnected network of computers which use a common protocol to communicate with one another
D. a world wide interconnected network of computers which use a common protocol to communicate with one another
3.Each computer connected to the internet must
- be an IBM PC
- have a unique IP address
- be internet compatible
- have a modem connection
B. have a unique IP address
4.To change xxxx@yyyy.edu to an IP address, we should use the _______ domain in the DNS protocol.
- generic
- country
- inverse
- none of the above
A. generic
5.IP address is currently
- 4 bytes long
- available in plenty
- 6 bytes long
- not assigned as it is all used up
A. 4 bytes long
6.To change xxxx@yyyy.zzzz.us to an IP address, we should use the _______ domain in the DNS protocol
- generic
- country
- inverse
- none of the above
B. country
7.IP addresses are converted to
- a binary string
- alphanumeric string
- a hierarchy of domain names
- a hexadecimal string
C. a hierarchy of domain names
8.To change an IP address to xxxx@yyyy.edu, we should use the _______ domain in the DNS protocol.
- generic
- country
- inverse
- none of the above
C. inverse
9.Internet addresses must always have at least
(i) a country name or organization type
(ii) internet service provider’s name
(iii) name of organization
(iv) name of individual
(v) type of organization
(i) a country name or organization type
(ii) internet service provider’s name
(iii) name of organization
(iv) name of individual
(v) type of organization
- i, ii, iii
- ii, iii, iv
- i, iii
- ii, iii, iv, v
C. i, iii
10.By Electronic Commerce we mean:
- Commerce of electronic goods
- Commerce which depends on electronics
- Commerce which is based on the use of internet
- Commerce which is based on transactions using computers connected by telecommunication network
D. Commerce which is based on transactions using computers connected by telecommunication network
Practice it now
1.Internet uses
- Packet switching
- Circuit switching
- Telephone switching
- Telex switching
A. Packet switching
2.For carrying out B2B e-Commerce the following infrastructure is essential:
I. World Wide Web
II. Corporate network
III. Electronic Data Interchange standards
IV. Secure Payment Services
V. Secure electronic communication link connecting businesses
I. World Wide Web
II. Corporate network
III. Electronic Data Interchange standards
IV. Secure Payment Services
V. Secure electronic communication link connecting businesses
- i, ii, iii
- ii, iii, iv
- ii, iii, iv, v
- i, ii, iii, iv, v
C. ii, iii, iv, v
3.Usually TCP/IP uses the services of _________ before using any other application program
- FTP
- DNS
- NVT
- none of the above
B. DNS
4.The domain xxxx@yyyy.com is a(n) _________ domain
- generic
- country
- inverse
- none of the above
A. generic
5.The domain xxxx@yyyy.gov is a(n) _________ domain.
- generic
- country
- inverse
- none of the above
A. generic
6.The domain xxxx@yyyy.fr is a(n) _________ domain
- generic
- country
- inverse
- none of the above
B. country
7.Internet data is broken up as
- fixed length packets
- variable length packets
- not packetized
- 64 bytes packets
B. variable length packets
8.Internet packet data structure consists of
I. source address
II. destination address
III. serial number of packets
IV. message bytes
V. Control bits for error checking
VI. Path identification bits
I. source address
II. destination address
III. serial number of packets
IV. message bytes
V. Control bits for error checking
VI. Path identification bits
- i, ii, iii
- i, ii, iii, iv
- i, ii, iii, iv, v
- i, ii, iii, iv, v, vi
C. i, ii, iii, iv, v
9.For carrying out B2C e-Commerce the following infrastructure is essential
i. World Wide Web
ii. Corporate network
iii. Electronic Data Interchange standards
iv. Secure Payment Services
v. Secure electronic communication link connecting businesses
i. World Wide Web
ii. Corporate network
iii. Electronic Data Interchange standards
iv. Secure Payment Services
v. Secure electronic communication link connecting businesses
- i, iv
- i, iii, iv
- ii, iii
- i, ii, iii, iv
A. i, iv
10.For carrying out C2C e-Commerce the followin
Computer Web Technologies Multiple Choice Questions Answers
1.The packets of an internet message
- take a predetermined path
- take a path based on packet priority
- go along different paths based on path availability
- take the shortest path from source to destination
C. go along different paths based on path availability
2.The domain 121.24.34.12.in-addr.arpa is a(n) _______ domain.
- generic
- country
- inverse
- none of the above
C. inverse
3.Advantages of B2C commerce are
(i) Business gets a wide reach to customers
(ii) Payment for services easy
(iii) Shop can be open 24 hours a day seven days a week
(iv) Privacy of transaction always maintained
(i) Business gets a wide reach to customers
(ii) Payment for services easy
(iii) Shop can be open 24 hours a day seven days a week
(iv) Privacy of transaction always maintained
- i and ii
- ii and iii
- i and iii
- iii and iv
C. i and iii
4.The time taken by internet packets
- can be predetermined before transmission
- may be different for different packets
- is irrelevant for audio packets
C. is irrelevant for audio packets
5.The general client-server program in the Internet is _________
- FTP
- TFTP
- TELNET
- none of the above
C. TELNET
6.B2C commerce
- includes services such as legal advice
- means only shopping for physical goods
- means only customers should approach customers to sell
- means only customers should approach business to buy
A. includes services such as legal advice
7.By an intranet we mean
- a LAN of an organization
- a Wide Area Network connecting all branches of an organization
- a corporate computer network
- a network connecting all computers of an organization and using the internet protocol
D. a network connecting all computers of an organization and using the internet protocol
8.The TELNET client uses a ________driver, while the TELNET server uses a _______ driver
- terminal; pseudoterminal
- pseudoterminal; terminal
- TELNET
- none of the above
A. terminal; pseudoterminal
9.Advantages of B2C commerce to customers are
(i) wide variety of goods can be accessed and comparative prices can be found
(ii) shopping can be done at any time
(iii) privacy of transactions can be guaranteed
(iv) security of transactions can be guaranteed
(i) wide variety of goods can be accessed and comparative prices can be found
(ii) shopping can be done at any time
(iii) privacy of transactions can be guaranteed
(iv) security of transactions can be guaranteed
- i and ii
- ii and iii
- iii and iv
- i and iv
A. i and ii
10.The FTP establishes _________ connection(s).
- one
- two
- three
- none of the above
B. two infrastructure is essential
i. World Wide Web
ii. Corporate network
iii. Electronic Data Interchange standards
iv. Secure Payment Services
v. Secure electronic communication link connecting businesses
i. World Wide Web
ii. Corporate network
iii. Electronic Data Interchange standards
iv. Secure Payment Services
v. Secure electronic communication link connecting businesses
- i and ii
- ii and iv
- i and iii
- i and iv
C. i and iii
Internet Basics Multiple Choice Questions Answers
1.Which connection is opened during the entire session in FTP?
- control
- data
- a and b
- neither a nor b
A. control Explanation :
2.Which connection is opened and closed during a session in FTP?
- control
- data
- a and b
- neither a nor b
B. data Explanation :
3.If the file to transfer is very large, we should use the services of _________.
- FTP
- TFTP
- a or b
- neither a nor b
A. FTP
4.Which protocol transfers a small file faster?
- FTP
- TFTP
- a or b
- neither a nor b
B. TFTP Explanation :
5.What is search engine optimization?
- Paying for placement on a search engine results page
- Building a site which has the qualities that search engines look for, which will ultimately get the site a high rank in the listings
- Optimization of a site so it gets more affiliate revenue
- Selling memberships to the site
B. Building a site which has the qualities that search engines look for, which will ultimately get the site a high rank in the listings
6.What are meta tags?
- The content of the site
- Embedded information about your website such as keywords
- Links to other sites
- Images on the site
B. Embedded information about your website such as keywords
7.What is meant by “web 2.0”?
- The resurgence of internet companies with more interactive focus, such as blogging and social networking
- Any website which has survived the dot.com bust
- Sites made using new technology
- Internet companies who focus on retail sales
A. The resurgence of internet companies with more interactive focus, such as blogging and social networking
8.In Electronic cash payment
(i) a customer withdraws “coins” in various denominations signed by the bank
(ii) the bank has a database of issued coins
(iii) the bank has a database of spent coins
(iv) the bank cannot trace a customer
(i) a customer withdraws “coins” in various denominations signed by the bank
(ii) the bank has a database of issued coins
(iii) the bank has a database of spent coins
(iv) the bank cannot trace a customer
- i, ii
- i, ii, iii
- i, ii, iii, iv
- ii, iii, iv
B. i, ii, iii
Introduction to Internet and WEB Technology MCQs
1.Electronic Data Interchange (EDI) standards are
- not universally available
- essential for B2B commerce
- not required for B2B commerce
- still being evolved
B. essential for B2B commerce Explanation :
2.The main protocol for sending e-mail in the TCP/IP protocol suite is called _____
- SMTP
- SNMP
- FTP
- none of the above
A. SMTP Explanation :
3.By an extranet we mean
- an extra fast computer network
- the intranets of two co-operating organizations interconnected via a secure leased line
- an extra network used by an organization for higher reliability
- an extra connection to internet provided to co-operating organization
B. the intranets of two co-operating organizations interconnected via a secure leased line
4.Electronic Data Interchange is necessary in
- B2C e-Commerce
- C2C e-Commerce
- B2B e-Commerce
- Commerce using internet
C. B2B e-Commerce
5.To transfer an e-mail to a private network, we need to have a
- mail router
- mail gateway
- mail agent
- none of the above
B. mail gateway
6.Electronic Data Interchange (EDI) requires
- representation of common business documents in computer readable forms
- data entry operators by receivers
- special value added networks
- special hardware at co-operating Business premises
A. representation of common business documents in computer readable forms
7.In SMTP, the entity that is used to prepare the message is called the ________
- MTA
- UA
- MA
- none of the above
B. UA Explanation :
8.World Wide Web
- is another name for internet
- world wide connection for computers
- a collection of linked information residing on computers connected by the internet
- a collection of world wide information
C. a collection of linked information residing on computers connected by the internet
9.In SMTP, the entity that is used to transfer the message is called the ________
- MTA
- UA
- MA
- none of the above
A. MTA Explanation :
10.In the destination e-mail address xxxx@yyyy.zzzz.tttt, _______ defines the local part of the destination
- tttt
- xxxx
- yyyy
- none of the above
B. xxxx
Internet and WEB Technology MCQs
1.Among services available on the World Wide Web are
(i)Encryption
(ii)HTTP
(iii)HTML
(iv)Firewalls
(i)Encryption
(ii)HTTP
(iii)HTML
(iv)Firewalls
- i and ii
- ii and iii
- iii and iv
- i and iv
B. ii and iii
2.In the destination e-mail address xxxx@yyyy.zzzz.tttt, _______ defines the domain name of the destination
- xxxx
- yyyy
- yyyy.zzzz.tttt
- none of the above
C. yyyy.zzzz.tttt
3.EDIFACT is a standard
- for representing business forms used in e-Commerce
- for e-mail transaction for e-Commerce
- for ftp in e-Commerce
- protocol used in e-Commerce
A. for representing business forms used in e-Commerce Explanation :
4.A world wide web contains web pages
- residing in many computers
- created using HTML
- with links to other web pages
- residing in many computers linked together using HTML
D. residing in many computers linked together using HTML
5.In an e-mail address, _______ separates the local part from the domain part
- @ (at sign)
- . (dot)
- # (pound sign)
- none of the above
A. @ (at sign)
6.EDIFACT standard was developed by
- American National Standard Institute
- International Standard Institute
- European Common Market
- United Nations Economic Commission for Europe
D. United Nations Economic Commission for Europe Explanation :
7.When an e-mail is sent, it is first stored in a(n) __________
- mailbox
- spool
- expander
- none of the above
B. spool
8.ANSI X.12 is a standard developed by
- American National Standard Institute
- International Standard Institute
- European Common Market
- United Nations Economic Commission for Europe
A. American National Standard Institute Explanation :
9.When an e-mail is received, it is first stored in a(n) __________
- mailbox
- spool
- expander
- none of the above
A. mailbox
10.In B2B e-Commerce
(i) Co-operating Business should give an EDI standard to be used
(ii) Programs must be developed to translate EDI forms to a form accepted by application program
(iii) Method of transmitting/receiving data should be mutually agreed
(iv) It is essential to use internet
(i) Co-operating Business should give an EDI standard to be used
(ii) Programs must be developed to translate EDI forms to a form accepted by application program
(iii) Method of transmitting/receiving data should be mutually agreed
(iv) It is essential to use internet
- i, ii
- i, ii, iii
- i, ii, iii, iv
- ii, iii, iv
B. i, ii, iii
Internet and WEB Technology Multiple Choice Questions Answers
1.The supplementary protocol that allows the use of non-ASCII characters in an e- mail is called the _________ protocol.
- MIME
- POP
- POP2
- none of the above
A. MIME Explanation :
2.The supplementary protocol that fetches e-mail from an e-mail server is called the _________ protocol
- MIME
- POP
- POP2
- none of the above
B. POP Explanation :
3.The official network management protocol in TCP/IP protocol suite is called _____
- SNTP
- SNMP
- SMTP
- none of the above
B. SNMP Explanation :
4.A manager station in SNMP is a __________.
- client
- server
- both a and b
- none of the above
A. client
5.An agent in SNMP is a __________
- client
- server
- both a and b
- none of the above
B. server
6.A web page is located using a
- Universal Record Linking
- Universal Resource Locator
- Universal Record Locator
- Uniformly Reachable Links
B. Universal Resource Locator
7.A URL specifies the following:
(i) protocol used
(ii) domain name of server hosting web page
(iii) name of folder with required information
(iv) name of document formatted using HTML
(v) the name of ISP
(i) protocol used
(ii) domain name of server hosting web page
(iii) name of folder with required information
(iv) name of document formatted using HTML
(v) the name of ISP
- i, ii, iii, iv
- ii, iii, iv, v
- i, iii, iv
- i, ii, iii, v
A. i, ii, iii, iv
8.A router is an example of a _______ in SNMP
- client
- server
- both a and b
- none of the above
B. server
9.Management in the Internet is achieved through _______ components.
- 1
- 2
- 3
- none of the above
C. 3
10.The management component in the Internet that is used to name the objects is called __________.
- SNMP
- SMI
- MIB
- none of the above
B. SMI Explanation :
Internet Technologies Basics MCQs
1.The management component in the Internet that creates a database of object is called _______
- SNMP
- SMI
- MIB
- none of the above
C. MIB Explanation :
2.The management component in the Internet that sends messages is called _______
- SNMP
- SMI
- MIB
- none of the above
A. SNMP Explanation :
3.A search engine is a program to search
- for information
- web pages
- web pages for specified index terms
- web pages for information using specified search terms
D. web pages for information using specified search terms
4.HTML stands for
- Hyper Text Making Links
- Hyper Text Markup Language
- Higher Textual Marking of Links
- Hyper Text Mixer of Links
B. Hyper Text Markup Language Explanation :
5.The second section of a request message in HTTP is the__________
- header
- request line
- body
- a blank line
A. header
6.The third section of a request message in HTTP is the__________
- header
- request line
- body
- a blank line
D. a blank line
7.An URL is normally made of _______ parts
- 3
- 4
- 2
- none of the above
B. 4
8.In the URL HTTP://xxxx:yyyy/zzzz, the method is _________.
- HTTP
- xxxx
- yyyy
- zzzz
A. HTTP
9.XLL definition is used along with XML to specify
- The data types of the contents of XML document
- The presentation of XML document
- The links with other documents
- The structure of XML document
C. The links with other documents Explanation :
10.DTD definition is used along with XML to specify
- The data types of the contents of XML document
- The presentation of XML document
- The links with other documents
- The structure of XML document
A. The data types of the contents of XML document Explanation :
Internet Technologies Basics Multiple Choice Questions Answers
1.In _______ each object is defined by a numeric identifier
- SNMP
- SMI
- MIB
- none of the above
C. MIB
2.The identifier for the object named sys under the mib object is ______.
- 1
- 1.3.6.1.2.1
- 1.3.6.1.2.1.1
- none of the above
C. 1.3.6.1.2.1.1
3.SNMP uses _________ messages to send and retrieve messages.
- 1
- 3
- 5
- none of the above
C. 5
4.If a manager needs to get some information from an agent, it uses the _______ message.
- GetRequest
- GetNextRequest
- SetRequest
- a or b
D. a or b
5.If an agent needs to send some information to a manager, it uses the _________ message
- GetRequest
- SetRequest
- GetResponse
- Trap
C. GetResponse
6.The first section of a response message in HTTP is the __________
- header
- status line
- body
- a blank line
B. status line
7.The fourth section of a response message in HTTP is the __________.
- header
- request line
- body
- a blank line
C. body
8.HTML is similar to a
- word processing language
- screen editor
- scripting language
- search engine
A. word processing language
9.Desirable properties of a website are
(i) a meaningful address
(ii) Help and search facilities
(iii) Links to related sites
(iv) Features to allow users to give feedback
(v) Hosting on a mainframe
(i) a meaningful address
(ii) Help and search facilities
(iii) Links to related sites
(iv) Features to allow users to give feedback
(v) Hosting on a mainframe
- i, ii, iii
- i, ii, iii, iv
- i, ii, iii, iv, v
- i, ii, iii, v
B. i, ii, iii, iv
10.XSL definition is used along with XML definition to specify
- The data types of the contents of XML document
- The presentation of XML document
- The links with other documents
- The structure of XML document
B. The presentation of XML document
Internet Basics Multiple Choice Questions and Answers
1.If a manager needs to change the setting of an agent, it uses the ____________ message
- GetRequest
- GetNextRequest
- SetRequest
- Trap
C. SetRequest
2.If an agent needs to report a situation to the manager, it uses the ___________ message
- GetRequest
- SetRequest
- GetResponse
- Trap
D. Trap
3.HTTP messages are divided into _______ categories
- 2
- 5
- 3
- none of the above
A. 2
4.A browser is an HTTP _________.
- client
- server
- agent
- none of the above
A. client
5.In HTTP, the message sent from the client to the server is called a ______.
- response
- request
- demand
- none of the above
B. request
6.HTML uses
- pre-specified tags
- user defined tags
- tags only for linking
- fixed tags defined by the language
D. fixed tags defined by the language
7.HTML tags define
- The data types of elements of document
- Presentation of specified elements of a document
- The contents of the document
- The structure of the document
B. Presentation of specified elements of a document
8.CGI is mostly associated with a _______ document.
- static
- dynamic
- active
- none of the above
B. dynamic
9.Java is mostly associated with a _______ document.
- static
- dynamic
- active
- none of the above
C. active
10.The advantages of XML over HTML are
(i) It allows processing of data stored in web-pages
(ii) It uses meaningful tags which aids in understanding the nature of a document
(iii) Is simpler than HTML
(iv)It separates presentation and structure of document
(i) It allows processing of data stored in web-pages
(ii) It uses meaningful tags which aids in understanding the nature of a document
(iii) Is simpler than HTML
(iv)It separates presentation and structure of document
- (i),(ii) and (iii)
- (i),(ii) and(iv)
- (ii),(iii) and (iv)
- (i),(iii) and (iv)
B. (i),(ii) and(iv)
Internet Fundamentals MCQs
1.In HTTP, the message sent from the server to the client is called a ______
- response
- request
- demand
- none of the above
A. response
2.A request or a response in HTTP is made of _______ components
- 3
- 4
- 2
- none of the above
B. 4
3.The first section of a request message in HTTP is the __________.
- header
- request line
- body
- a blank line
B. request line
4.The tag used in HTML to link it with other URL’s is
- “<A>”
- “<H>”
- “<U>”
- “<L>”
A. “<A>”
5.The tags used for specifying fonts BOLD and Italic in HTML are
(i) “<B>”
(ii) “<I>”
(iii) “<U>”
(iv) “<L>”
(i) “<B>”
(ii) “<I>”
(iii) “<U>”
(iv) “<L>”
- (i) and (ii)
- (i) and (iii)
- (ii) and (iv)
- (i),(ii) and (iii)
A. “<A>”
6.A web page document that is stored in the server and can be retrieved by a browser is called a _______ document
- static
- dynamic
- active
- none of the above
A. static
7.A web page document that is stored in the server but should be run before the result can be retrieved by a browser is called a _______ document.
- static
- dynamic
- active
- none of the above
B. dynamic
8.HTML is mostly associated with a _______ document
- static
- dynamic
- active
- none of the above
A. static
9.XML uses
- user define tags
- pre-defined tags
- both predefined and user-defined tags
- Extended tags used in HTML and makes them powerful
A. user define tags
10.In order to interpret XML documents one should
- Use standardized tags
- Have a document type definition which defines the tags
- Define the tags separately
- Specify tag filename
B. Have a document type definition which defines the tags
Web/Internet Basics MCQs
1.The four section of a request message in HTTP is the __________
- header
- request line
- body
- a blank line
C. body
2.It is possible to display pictures (i.e, images) in HTML specification by using the tag
- “<GR src = Picture file>”
- “<PIC src =Picture file>”
- “<IMG src =Picture file>”
- “<GIF src=Picture file>”
C. “<IMG src =Picture file>”
3.SGML stands for
- Standard Generalized Markup Language
- Structured General Markup Language
- Standard Graphics Mapping Language
- Standard General Markup Link
A. Standard Generalized Markup Language
4.In the URL HTTP://xxxx:yyyy/zzzz, the name of the host (or an alias for it) is _________
- HTTP
- xxxx
- yyyy
- zzzz
B. xxxx
5.In the URL HTTP://xxxx:yyyy/zzzz, the name of the port is _________.
- HTTP
- xxxx
- yyyy
- zzzz
C. yyyy
6.In the URL HTTP://xxxx:yyyy/zzzz, the pathname of the file or directory where the web page is located is _______
- HTTP
- xxxx
- yyyy
- zzzz
D. zzzz
7.HTML and XML are markup languages
- Specially development for the web
- Are based on SGML
- Are versions of SGML
- Independent of SGML
B. Are based on SGML











COMMENTS